Referential Labs Blog
Learn from the best. Our blog is full of tips and tricks to help you deliver your software. When you need a little more help, we're here for you.

Lessons Learned Building RAG Systems for Many Clients
Struggling with RAG systems? Learn from a performance engineer's insights. Discover strategies for better recall, scalability, and customization. Contact Referential Labs for tailored solutions.

API-First
APIs enable software interoperability through abstraction. A sound API strategy focuses on security, reliability, documentation, and governance to efficiently share data and capabilities.

From VPNs to Zero Trust
Securing dynamic cloud networks with identity-centric, context-aware access controls instead of static VPN perimeters.

Test Driven Infrastructure with varnishtest
Learn how to implement test driven infrastructure configs with CI/CD pipelines for reliable and rapid delivery, varnishtest for automated testing of edge logic in Varnish

11 Varnish Web Acceleration Techniques Shield Your Slow Legacy Web Application
Struggling with a legacy web app that can't handle modern traffic? Before embarking on a risky rewrite, explore clever caching techniques to accelerate your aging application. This post reveals how to tune Varnish to achieve over 90% cache hit rates, reduce backend load, and optimize performance of your legacy code without engineering changes. Follow our battle-tested guide to caching strategies that buy time and deliver lasting relief for your vintage but valuable application.
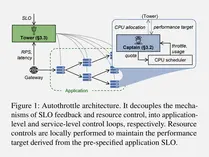
Autothrottle: Manage Resources for SLO-Targeted Microservices
Efficiently managing resources for latency-sensitive microservices applications is challenging. Autothrottle is a new approach to resource management for microservices.

HTTP Load Balancing with NGINX
A comprehensive guide walking through HTTP load balancing with NGINX and explains how to distribute requests across multiple backend servers using different methods.
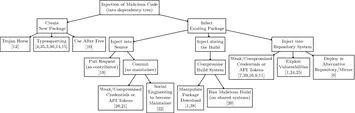
Open Source Software Supply Chain Attacks Review
This paper examines best practices for improving software supply chain security through a DevSecOps approach. As software supply chain attacks exploiting vulnerabilities in open source components increase, organizations need better methods to secure their code dependencies. The paper recommends techniques like maintaining a comprehensive inventory of open source libraries, prioritizing security updates, utilizing dependency analysis tools, establishing software integrity controls, and monitoring for emerging dependency threats.

