Open Source Software Supply Chain Attacks Review
3 minutes read (576 words)
August 11th, 2020
In this is post we will walk through the research paper Backstabber's Knife Collection: A Review of Open Source Software Supply Chain Attacks.
Backstabber's Knife Collection: A Review of Open Source Software Supply Chain Attacks
A single open source package may be required by several thousands of open source software projects, which makes open source packages a very attractive target for software supply chain attacks. A recent attack on the npm package event-stream demonstrates the potential reach of such attacks: The alleged attacker was granted ownership of a prominent npm package simply by asking the original developer to take over its maintenance. At that time, event-stream was used by another 1,600 packages, and was on average downloaded 1.5 million times a week. Open source software supply chain attacks are comparable to the problem of vulnerable open source packages which may pass their vulnerability to dependent software projects.
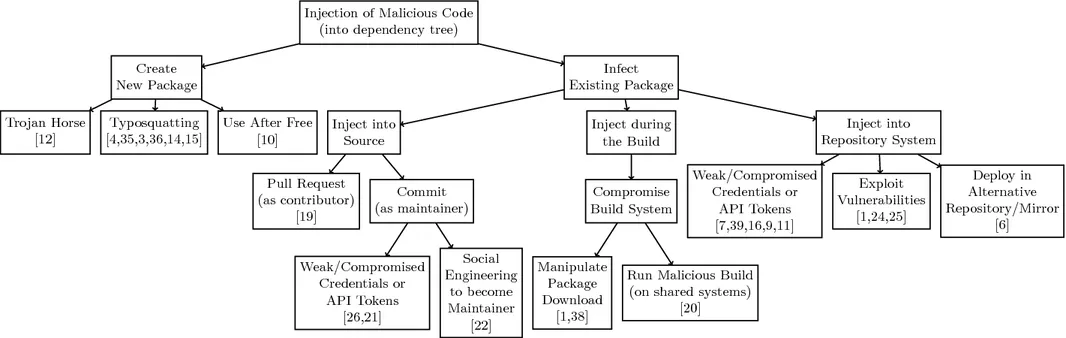
Last month in Lecture Notes in Computer Science, vol 12223, Ohm, Plate, Sykosch and Meier published Backstabber’s Knife Collection: A Review of Open Source Software Supply Chain Attacks.
As a keen practitioner of improving software supply chains for Referential Labs' customers, I immediately pounced on the chapter. Here are seven key takeaways from the article with respect to advice to reduce software supply chain vulnerabilities:
- Software supply chain attacks are increasing, exploiting vulnerabilities in third-party components integrated into applications. This highlights the need for better software supply chain security practices.
- Know your dependencies - Maintain a comprehensive inventory of all third-party libraries, modules, and components used. Monitor them for vulnerabilities.
- Perform thorough due diligence on suppliers and third-party code before integrating into your software. Assess their security practices.
- Prioritize applying security updates for vulnerable dependencies quickly. Have processes to expedite patching.
- Use dependency analysis tools to detect vulnerabilities in third-party code and enforce open source policies. Integrate into build process.
- Validate integrity of dependencies downloaded. Use curated repositories and registries you trust.
- Utilize dependency graphs to analyze risk exposure from transitive dependencies. Remove unnecessary dependencies.
- Implement software integrity controls like reproducible builds to detect tampering. Sign code at build time.
- Monitor emerging threats to third-party code and have response plans to address vulnerabilities rapidly.
- Adopt DevSecOps model to make security a shared responsibility between developers, ops, and security teams.
What on earth is DevSecOps?
In the context of improving software supply chain security, DevSecOps:
- integrates security practices throughout the software development lifecycle, bringing security closer to developers and development workflows.
- has Security teams provide guardrails, tools, and automation to help developers build in security rather than relying solely on retroactive audits.
- includes Security team members early in requirements gathering to identify risks. Threat modeling is performed on designs.
- integrates static and dynamic analysis tools into builds to catch vulnerabilities and misconfigurations early.
- embeds good security defaults into Infrastructure as code and policy as code and automate provisioning and configuration of environments leveraging these.
- integrates security testing into CI/CD pipelines to validate controls and catch regressions.
- monitors for drift and anomalies during runtime can identify supply chain attacks in progress.
- focus security teams efforts on providing enablement, guidance and oversight rather than enforcement.
- increases collaboration between development, security, and operations using a shared responsibility model.
- integrates security into developer workflows helps to reduce friction and improve outcomes and automate policy enforcement.
The main goal of DevSecOps is to make building secure software an integral part of daily work for developers rather than an afterthought. It results in more secure software supply chains.
Is your small organization struggling to build in security? With our DevSecOps subscription service, you get the expertise and bandwidth that you need to securely develop software without compromising speed or quality.
With DevSecOps as a Service, you’ll be releasing more robust code more frequently. Tighten up your software supply chain security with the guiding hand of our DevSecOps expertise and experience behind you.